Welcome to Day 55 of the #100DaysOfDevOps Challenge! Today we will deep dive into Subnetting in AWS
Subnets allow for effective IP address distribution. These are segments of a larger network that often reside within a private network.
You can manage IP address ranges more easily by dividing them up into smaller, easier-to-manage blocks. Subnets are restricted to one Availability Zone.
You can protect your applications from single Availability Zone failure by launching AWS resources in different Availability Zones.
When you create a subnet, you specify its IP addresses, depending on the configuration of the VPC
When configuring your VPC’s IP addresses, it’s important to note whether you are working with IPv4-only, dual-stack, or IPv6-only subnets.
In an IPv4-only subnet, communication must be done over IPv4 as there is no IPv6 CIDR block available.
Dual-stack subnets have both IPv4 and IPv6 CIDR blocks, allowing for communication over both protocols.
Finally, in an IPv6-only subnet, communication must be done over IPv6 as there is no IPv4 CIDR block available. Make sure to properly configure your VPC to avoid any potential connectivity issues.
Subnet Masks
A subnet mask is a 32-bit address that divides an IP address into network and host bits. The network bits identify the network, while the host bits identify the device on that network. This allows for the creation of smaller networks within a larger network, known as subnets.
Subnet mask representation
When a new device connects to a network, it is assigned an IPv4 address which is a 32-bit numeric address separated into four numbers by periods. Each group of numbers within a block is called an octet, and its value ranges from 0 to 255. Without the subnet mask, the network and host portions of such IP addresses become indistinguishable
Let’s look at an example, Consider the IP address for my device: 192.168.112.121 –> 11000000.10101000. 01110000. 01111001
The subnet mask for the IP network above: 255.255.255.0 –> 11111111. 11111111. 11111111. 00000000
Using this example, a household home network has a subnet mask of 255.255.255.0. This means that within the defined network, 254 IP addresses are usable. To put it simply, you can connect up to 254 internet-enabled devices such as phones, computers, IoT gadgets, and many others to the home network, and can access the internet using them.
Subnet Types
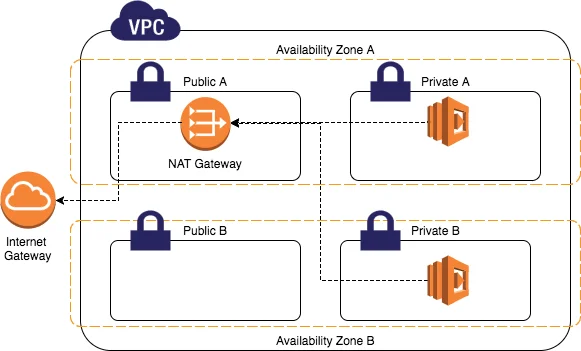
When configuring your subnet’s routing, the type of subnet you end up with will depend on your choices. For instance:
When creating subnets in your VPC, it’s crucial to consider their internet connectivity.
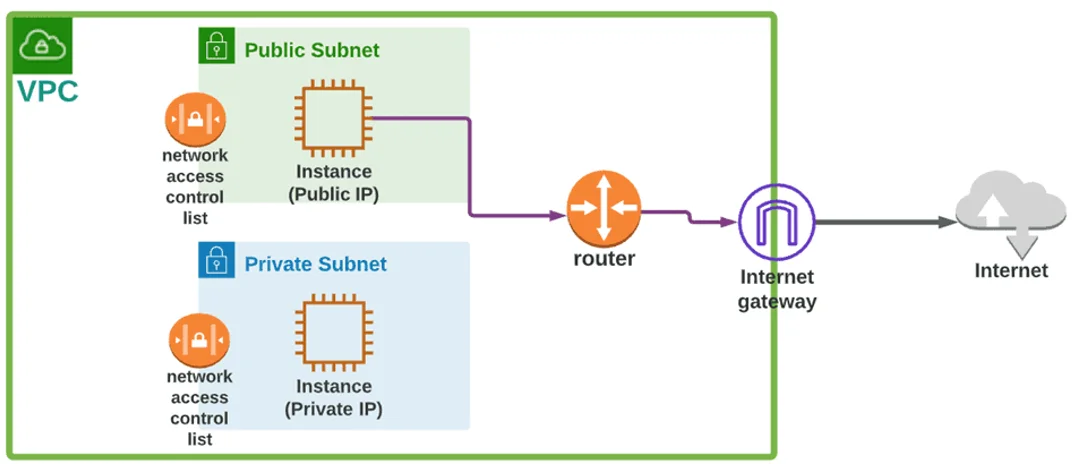
A public subnet enables resources to access the internet directly via an internet gateway.
A private subnet requires a NAT device for internet access.
A VPN-only subnet has a route to a Site-to-Site VPN connection, but no access to the internet gateway.
An isolated subnet has no external connectivity and can only be reached within the VPC.
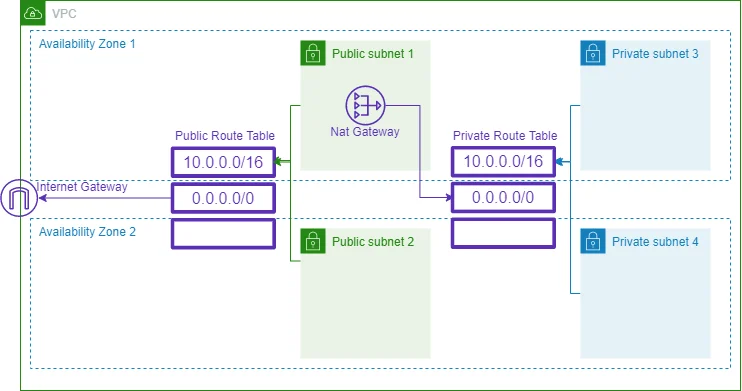
Subnet Routing
Each subnet is associated with a route table that specifies allowed outbound traffic routes. All subnets are initially associated with the VPC’s main route table, but you can change this association and the contents of the main route table.
Subnet Settings
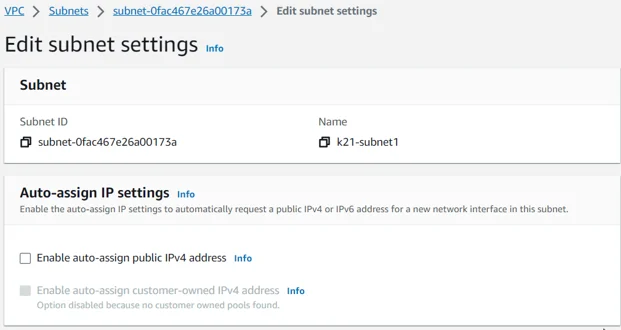
Every subnet possesses an alterable attribute that decides if a network interface created within it gets assigned a public IPv4 address and, if applicable, an IPv6 address. This includes the primary network interface (eth0) that is generated when you initiate an instance in that subnet. Nevertheless, it is imperative to note that this setting can be overridden for a specific instance during launch.
To configure the auto-assign IP settings for a new network interface in a subnet, there are two ways.
You can enable the Auto-assign IP settings option. This will allow you to request a public IPv4 or IPv6 address automatically.
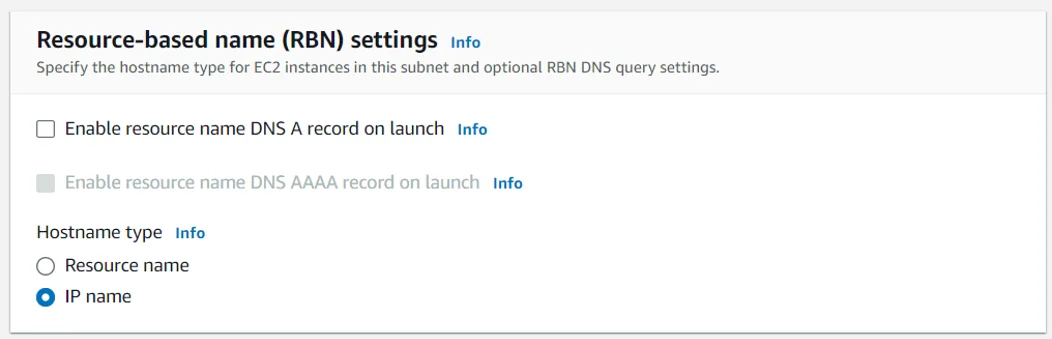
You can configure the Resource-based Name (RBN) settings to specify the hostname type for EC2 instances in the subnet and configure how DNS queries are handled for A and AAAA records. For more information on hostname types for EC2 instances.
AWS VPC and Subnet Security
To protect your AWS VPC and Subnet resources, it is recommended that you use private subnets. We can use a bastion host or NAT device to provide internet access to resources, such as EC2 instances, in a private subnet.
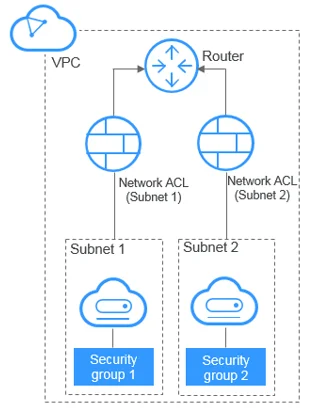
To increase security for the resources in your VPC, AWS offers security groups and network ACLs.
Security groups permit inbound and outbound traffic for associated resources, while network ACLs allow or deny traffic at the subnet level.
Keep in mind that using private subnets with a bastion host or NAT device is necessary to grant internet access to EC2 instances in private subnets.
Conclusion: AWS VPC and Subnets
AWS VPC and subnets provide a secure and efficient foundation for organizing cloud resources. Understanding VPC concepts enables designing networks aligned with specific needs while offering the cloud’s scalability and isolation advantages
