Services in AWS for a DevOps Engineer
As of March 2024, there are over 200+ AWS services available. In those 200+ services, a few services that you may use as a DevOps Engineer are:
Compute: EC2, ECS, Lambda, Fargate, EKS.
Storage: S3, RDS, DynamoDB, ElastiCache.
Networking: VPC, Route53, CloudFront.
Security: IAM, KMS, Secrets Manager.
DevOps: CodeBuild, CodePipeline, CodeCommit, CodeDeploy.
Logging & Monitoring: CloudWatch, OpenSearch, CloudTrail.
AWS - IAM
IAM is the abbreviation of Identity Access Management. It provides centralized control and management of user access to AWS resources.
IAM enables you to securely manage user identities, permissions, and authentication for your AWS environment.
IAM allows you to create and manage AWS user accounts, groups, and roles, and assign permissions to control access to various AWS resources and services.
With IAM, you can define fine-grained access policies that specify which actions users or roles can perform on specific resources.

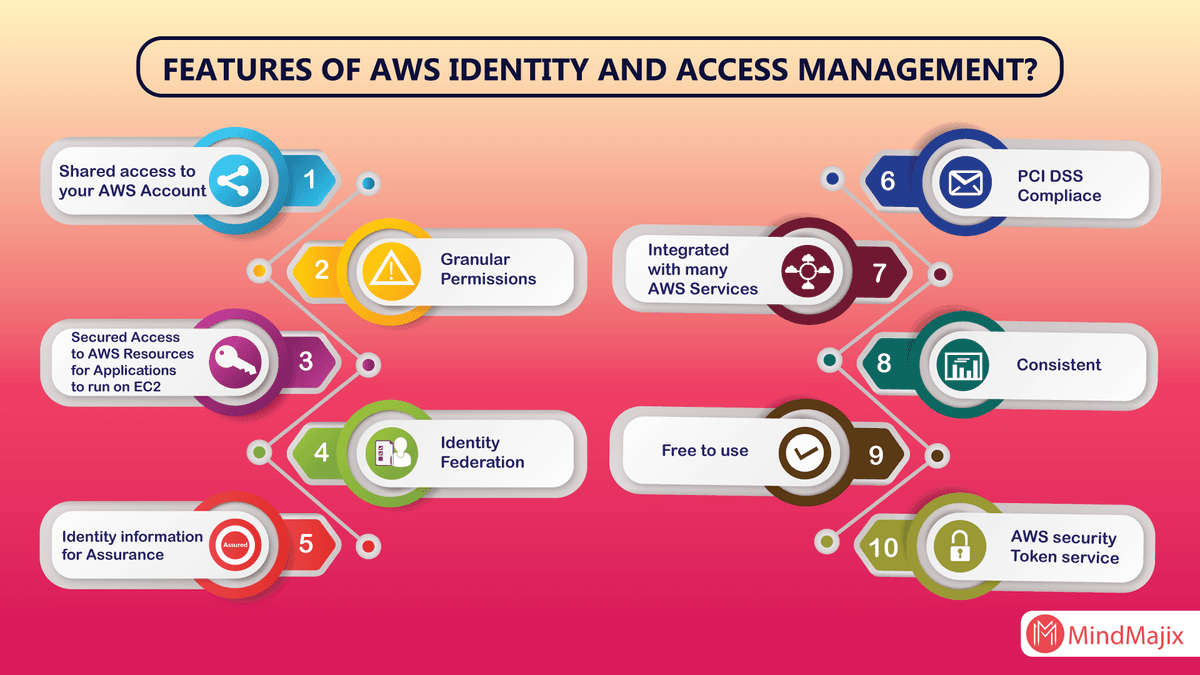
IAM Key Points
IAM controls access to AWS services and resources.
IAM enables access between AWS services (e.g. EC2 to RDS).
The main feature of IAM is that it allows you to create separate usernames and passwords for individual users or resources and delegate access.
IAM supports identity federation. If the user is already authenticated, such as through a Facebook or Google account, IAM can be made to trust that authentication method and then allow access based on it.
IAM is a free service. There is no additional charge for IAM security. There is no additional charge for creating additional users, groups, or policies.
IAM is PCI DSS compliance.
IAM supports MFA.
It provides two essential functions that work together:
Authentication:
Validates the identity of a user or a service.
Create and manage IAM identities.
Federate corporate identities.
Authorization:
Defines the permissions and limits access to only specific resources for the permitted user.
Assign permissions to IAM identities.
Assign permissions to corporate identities.
Let’s perform a few tasks so that we can understand what IAM is before completely dwelling on the theory part.
Tasks
Login to your AWS Console as a root user.

Task 1: Create an IAM user with the username of your wish
Search for IAM in the search bar. The IAM dashboard like the below one appears:
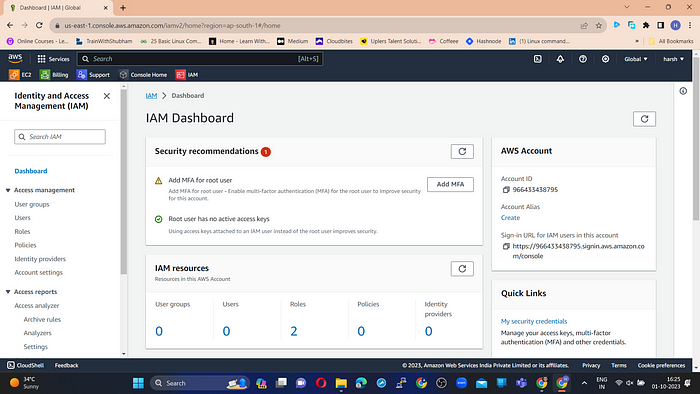
In the left corner, you can see Access Management. Go to Users.

Click on Add Users.
Step 1: Specify user details
Provide the username you want.
Select the checkbox for “Provide user access to the AWS Management Console — optional”.
Select “I want to create an IAM user”
Click on Next.



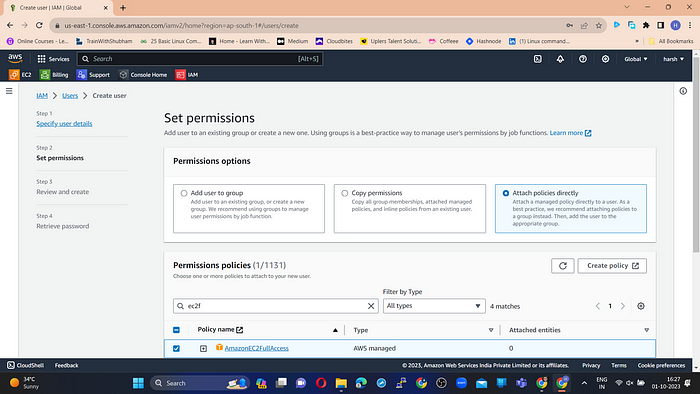
Step 2: Set permissions
Select “Attach policies directly” in the Permission Options.
In the Permission Policies search bar, search for EC2 and select “AmazonEC2FullAccess”.
Click on Next.
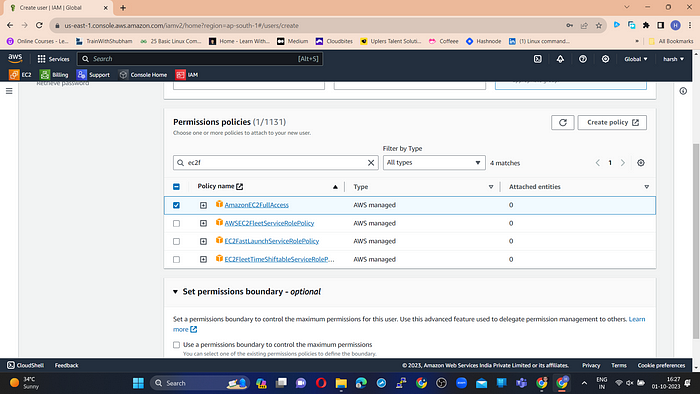

Step 3: Review and create
Review the details and click on “Create User”.

Step 4: Retrieve the password
You can view and download the user’s password below or email the user’s instructions for signing in to the AWS Management Console. This is the only time you can view and download this password.

Make it a point to download the .csv file, if you are not accessing the AWS through IAM user immediately.
Click on Return to User’s list.

Let’s log in to AWS as an IAM user. Open in any other browser.
Account ID will be the 12-digit number we had in the console sign-in URL.

Log in using the Account ID.

Now sign in as an IAM user using the username and password that you have downloaded as a .csv file.

You will be asked to reset the password. Go ahead and change the password using the details you have.

After password creation, we can able to access the AWS console and its Services

