Intro to AWS VPC
VPC stands for Virtual Private Cloud, which is a virtual network infrastructure provided by Amazon Web Services (AWS). It enables you to create a logically isolated section of the AWS cloud where you can launch resources such as EC2 instances, RDS databases, and more.
A VPC allows you complete control over your network configuration, including IP address ranges, subnets, and routing tables. You can also create security groups and network access control lists (ACLs) to control traffic to and from your instances.
The benefit of VPC is that it helps in aspects of cloud computing like privacy, security, and preventing loss of proprietary data.
The following diagram shows an example of VPC. The VPC has one subnet in each of the Availability Zones in the Region, EC2 instances in each subnet, and an internet gateway to allow communication between the resources in your VPC and the internet.
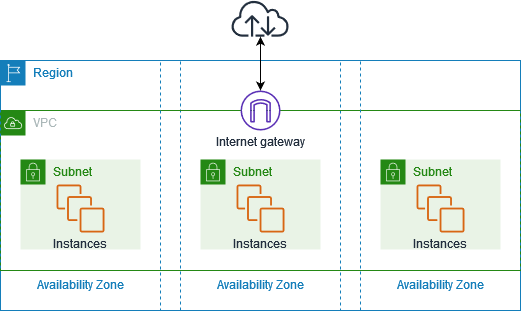
Let's take a look at some of the basics of a VPC
Subnets: A subnet can be thought of as dividing a large network into smaller networks. This is done because the maintenance of smaller networks is easier and it also provides security to the network from other networks.
Route Tables: A route table contains a set of rules called routes which determine where traffic has to be directed. You can have multiple route tables in a VPC.
Internet Gateways (IGW): It is a combination of hardware and software that provides your private networks with a route to the world outside.
An IGW is a horizontally scaled, redundant, and highly available VPC component that allows communication between instances and the internet. Only one IGW can be attached to a VPC at a time.
Network Address Translation (NAT): Since the subnet is private, the IP addresses assigned to the instances cannot be used in public. NAT maps the private IP addresses to the public address on the way out and vice versa on the way in. An Elastic IP address is a static, public IPv4 address designed for dynamic cloud computing. You can associate an Elastic IP address with any instance or network interface for any VPC in your account. With an Elastic IP address, you can mask the failure of an instance by rapidly remapping the address to another instance in your VPC.
Security groups: Security groups are a set of firewall rules that control the traffic for your instance. In Amazon Firewall the only action that can be carried out is allow. You cannot create a rule to deny. The destination is always the instance on which the service security group is running. You can have a single security group associated with multiple instances.
Customer Gateway — An Amazon VPC VPN connection links your data center (or network) to your Amazon VPC (virtual private cloud). A customer gateway is the anchor on your side of that connection. It can be a physical or software appliance.
Virtual Private Gateway — A virtual private gateway is the VPN concentrator on the Amazon side of the VPN connection. You create a virtual private gateway and attach it to the VPC from which you want to create the VPN connection.
VPN stands for ‘virtual private networking’, which is a popular internet security method that was originally designed for large organizations where employees needed to connect to a certain computer from different locations.
VPC Peering — A VPC peering connection allows you to route traffic between two VPC’s using IPv4 or IPv6 private addresses. Instances in either VPC can communicate with each other as if they are within the same network. You can create a VPC peering connection between your VPCs, or with a VPC in another AWS account. A VPC peering connection helps you to facilitate the transfer of data.
Network Access Control Lists (NACL)— an optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets. You might set up network ACLs with rules similar to your security groups to add layer of security to your VPC. The default network ACL is configured to allow all traffic to flow in and out of the subnets to which it is associated.
Getting started with Amazon VPC
Your AWS account includes a default VPC in each AWS Region. Your default VPCs are configured such that you can immediately start launching and connecting to EC2 instances. For more information, see Get Started with Amazon VPC.
You can choose to create additional VPCs with the subnets, IP addresses, gateways, and routing that you need. For more information, see Create a VPC.
Step 1 — Open the AWS account, search VPC in the search bar and click on VPC

Before creating your own VPC, let's understand about default VPC
By default, when you create a new AWS account, a default VPC (Virtual Private Cloud) is created for you in each AWS region. The default VPC is a logically isolated virtual network within the AWS Cloud that you can use to launch your AWS resources, such as EC2 instances, RDS databases, and more.
The default VPC comes preconfigured with several default settings, including an Internet Gateway and a default subnet in each Availability Zone within the region. This means that you can launch your resources in the default VPC without having to worry about configuring networking settings.

Step 2 — Click on Create VPC, select VPC only and enter IPv4.

A Main Route table will be created automatically but it has only local in the target group.

Create a Public Subnet in your Custom VPC
What is a Public Subnet?
A public subnet is a portion of a computer network that is accessible from the Internet, meaning it has a public IP address that can be reached by anyone on the Internet. In a public subnet, resources like web servers, email servers, and other services that need to be publicly accessible are typically deployed.
Public subnets are often used in cloud computing environments like Amazon Web Services (AWS), where they are paired with a private subnet to create a virtual private cloud (VPC). The private subnet is used to host resources that should not be accessible from the Internet, such as databases, backend servers, and internal applications.

In the above pic, you can see subnets that are created by AWS when default VPC is created.
Step 1 — Click on Create subnet, select your custom VPC, Give a name to the subnet, select Availability zone according to your convince and assign IPV4 CDIR block to this subnet.

Step 2 — Make Auto-assign IP enable because as name suggests it is a Public subnet.

Step 3 — Create an Internet gateway to your Custom VPC
What is an Internet Gateway?
An Internet Gateway (IGW) is a horizontally scaled, redundant, and highly available component in Amazon Web Services (AWS) that allows communication between resources in a VPC and the Internet.
An Internet Gateway is a virtual router that connects a VPC to the Internet. It provides a target for traffic destined for the public internet from instances in the VPC and a source for traffic originating from the internet and intended for instances in the VPC.
It is an AWS-managed component attached to your VPC and Its acts as a gateway between your VPC & the internet, basically the outside world.

In the above pic, you can see an internet gateway already created which is created by AWS when default VPC is created.
Click on Create Internet Gateway, give a name to it, and create an Internet gateway

Now, Attach this internet gate to your custom VPC



Step 4 — Add Internet way id to main route table
What is Route table ?
In Amazon Web Services (AWS), the main route table is the default route table that is created when you create a VPC. Every subnet that you create in the VPC is associated with this default route table unless you explicitly associate it with a custom route table.
The main route table contains rules that define how traffic is directed within the VPC. It is used to route traffic between subnets within the VPC and to control access to and from the internet. By default, the main route table has a route that sends all traffic to a local route for communication within the VPC.
You can add, modify or delete the routes in the main route table to control the flow of traffic within your VPC. For example, you can add a route that sends traffic to an Internet Gateway to allow resources in a public subnet to access the internet. You can also add a route that sends traffic to a NAT Gateway to allow resources in a private subnet to access the internet.

Select route table and go to edit routes in that add destination as 0.0.0.0/0 and past your internet gateway id in target and save the changes.

Create an Ec2 instance in the public subnet of a custom VPC
Give a name to that instance, select instance type, create a key pair, and in the network setting , select your custom VPC and public subnet it.

AWS provides a number of efficient, secure connectivity options to help you get the most out of AWS when integrating your remote networks with Amazon VPC. Amazon Virtual Private Cloud (Amazon VPC) enables you to launch AWS resources into a virtual network that you’ve defined. This virtual network closely resembles a traditional network that you’d operate in your own data center, with the benefits of using the scalable infrastructure of AWS.
